Securing Critical Data: Strategies for Protecting Sensitive Information
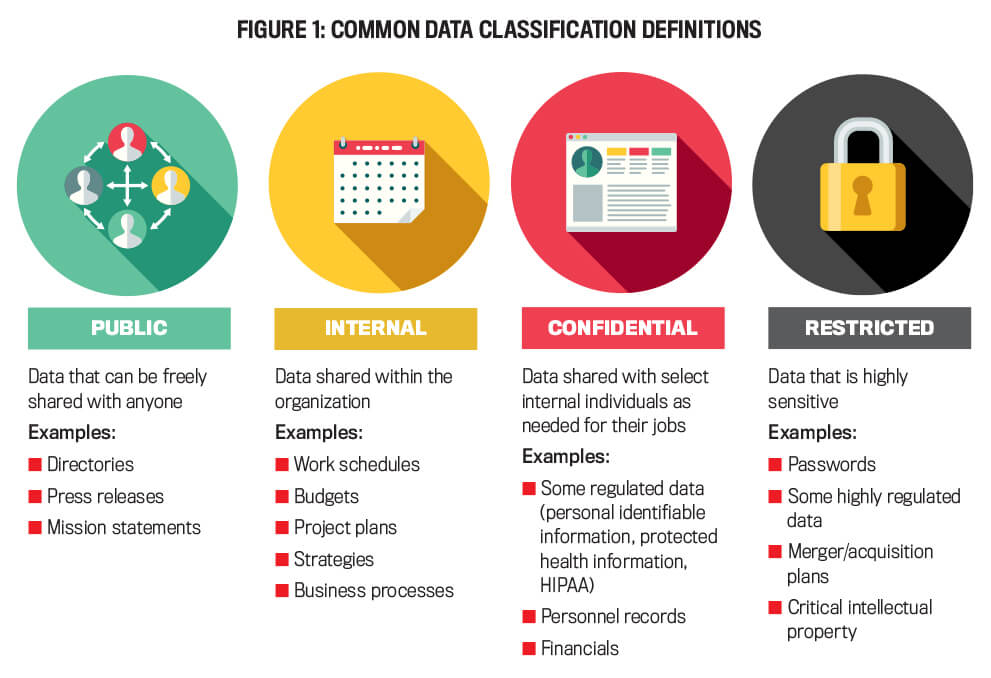
23Fairbet, Golden77: Properly categorizing data is a fundamental aspect of information management within organizations. Data classification involves organizing information into different groups based on their level of sensitivity, importance, or regulatory requirements. By assigning specific categories to data, organizations can implement appropriate security measures and controls to protect valuable information and minimize the risk of unauthorized access or data breaches.
Categorizing data also enables organizations to streamline their data handling processes, making it easier to locate and retrieve information when needed. Through data classification, organizations can prioritize their resources and efforts towards securing their most critical data assets. Additionally, data classification helps in compliance with data protection regulations by ensuring that sensitive information is appropriately protected and handled according to legal requirements.
Encryption Techniques: Implementing Strong Security Measures to Safeguard Data
Organizations today face increasing challenges in securing their sensitive data from cyber threats. Encryption techniques play a crucial role in safeguarding data by converting it into a format that only authorized parties can understand. By implementing strong encryption measures, organizations can mitigate the risk of data breaches and protect valuable information from falling into the wrong hands.
Strong encryption ensures that even if data is intercepted during transmission or stored in unauthorized locations, it remains indecipherable to unauthorized parties. This provides an added layer of security, helping organizations comply with data protection regulations and build trust with their customers. By adopting encryption techniques as part of their security strategy, organizations can enhance their overall cybersecurity posture and better safeguard their valuable data assets.
Access Control: Restricting Unauthorized Access to Sensitive Information
Access control plays a crucial role in ensuring the security of sensitive data within an organization. By implementing strict access control measures, businesses can effectively restrict unauthorized individuals from gaining entry to confidential information. This not only helps prevent data breaches but also safeguards the integrity and confidentiality of critical data assets.
Through the use of access control mechanisms such as authentication, authorization, and audit trails, organizations can establish granular control over who has access to specific data sets. By defining access levels and permissions for different user roles, companies can limit the exposure of sensitive information to only those individuals who require it for their job responsibilities. This proactive approach to access control strengthens the overall security posture of an organization and reduces the risk of data leaks or unauthorized access incidents.
• Authentication, authorization, and audit trails are key access control mechanisms
• Establishing granular control over data access helps limit exposure of sensitive information
• Defining access levels and permissions for different user roles enhances security posture
• Proactive approach to access control reduces risk of data leaks or unauthorized access incidents
Network Security: Protecting Data During Transmission Across Networks
Data transmission across networks is a critical aspect of modern information sharing. As data flows through various network nodes, there is a constant risk of interception by unauthorized parties. To safeguard data during transmission, encryption plays a vital role in securing the information from potential breaches. By converting data into a coded format that can only be deciphered by authorized recipients, encryption ensures that sensitive information remains confidential and protected from cyber threats.
In addition to encryption, other security measures such as virtual private networks (VPNs) and secure sockets layer (SSL) protocols are utilized to enhance the security of data during transmission. VPNs create a secure encrypted connection over a less secure network, allowing users to securely access private networks from remote locations. Meanwhile, SSL protocols establish a secure connection between a user’s web browser and the server, ensuring that data exchanged between the two points remains encrypted and protected from eavesdropping. These security measures collectively work to safeguard data as it travels across networks, mitigating the risk of unauthorized access and ensuring the confidentiality of sensitive information.
Why is data classification important in network security?
Data classification is important in network security because it helps to identify the sensitivity of information and determine the level of protection needed to safeguard it.
What are some common encryption techniques used to secure data during transmission across networks?
Some common encryption techniques include SSL/TLS, IPsec, and VPNs, which help to ensure that data is securely encrypted and protected from unauthorized access.
How does access control help in protecting sensitive information in a network?
Access control helps in protecting sensitive information by restricting unauthorized access to data, ensuring that only authorized users can view or modify the information.
What are some best practices for network security to protect data during transmission?
Some best practices for network security include regularly updating security protocols, using strong encryption algorithms, implementing access control measures, and monitoring network traffic for any suspicious activity.